

While the large corporations always make the headline news, small and medium sized businesses are prime targets for cybercrime because they often lack the knowledge and resources to protect themselves from the ever-evolving threats targeting their information.
Statistics show 1 out of 10 small-midsize businesses will be a victim of a cyber attack every year.

Many businesses feel safe because they have a "tool" installed on their computer that is supposed to take care of their cybersecurity.
But proper cybersecurity requires 24/7 vigilance and constant adaptation that one-and-done software cannot provide. Leapfrog provides the benefit of a full service security team to your business to deliver uniquely effective solutions.

Leapfrog is an MSSP (Managed Security Service Provider) that offers a wide range of cybersecurity services to organizations of all sizes. As an MSSP, Leapfrog provides its clients with comprehensive, expert security solutions that are designed to help protect against the constantly evolving threats in the technology industry.
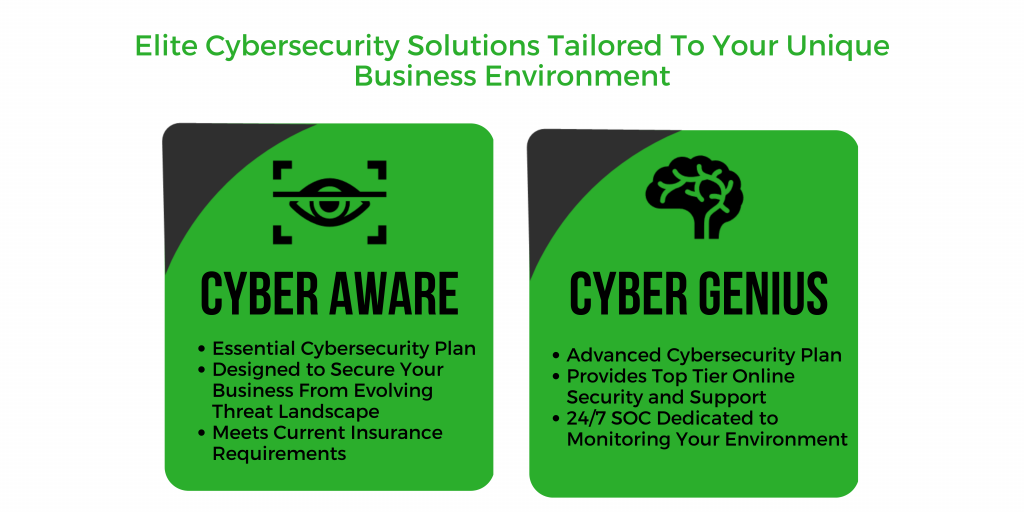
- Security Focused - While a traditional MSP (Managed Service Provider) may offer some basic security services, an MSSP like Leapfrog provides a more comprehensive solution that goes beyond just desktop antivirus and network monitoring.
- Proactive Approach - By partnering with an MSSP, companies can take a proactive approach to cybersecurity, rather than relying on reactive measures after a security breach has occurred.
- Capable Experts - MSSPs like Leapfrog have the necessary tools, technologies, and threat intelligence to stay ahead of the latest threats, and they are equipped to handle more complex security incidents that might otherwise overwhelm a traditional IT team.
- Incomparable Low Costs - When you partner with Leapfrog as your MSSP, you get the benefit of a full security team at your fingertips for a fraction of the cost of even ONE internal dedicated information security employee. This means broader expertise and greater productivity for a much lower cost.

Cybersecurity should be a top priority for every business, as the threat landscape continues to evolve and grow more sophisticated.
- Increasing Risk With Devastating Consequences - With ransomware, phishing attacks and data theft affecting companies all around the world on a daily basis, it is not a question of IF your business falls victim, it's a question of WHEN, and how extensive the damage will be in its wake.
- Increasing Pressure From Insurance Companies - Not only are businesses facing an increasing number of cyber threats, but insurance companies are also placing greater emphasis on the need for robust cybersecurity protections. Companies that don't take cybersecurity seriously are at risk of suffering significant financial losses, as well as damaging their reputation, if they fall victim to a cyberattack. Insurance companies are aware of these risks and are increasingly requiring businesses to have robust security measures in place in order to be eligible for coverage.
Leapfrog's goal is to provide your business with the highest level of protection possible, while also keeping your unique needs and budget in mind.

For companies that store customer data, private health or financial information, or process credit card transactions, network security is no longer an option, but a necessity. With cyberattacks becoming increasingly sophisticated and frequent, it's crucial for businesses to protect themselves and their customers' sensitive information.
Moreover, if a company must adhere to regulations such as HIPAA, PCI, SOC, or any other industry-specific standards, network security is even more critical. In these cases, companies must have a team in place that understands the specific requirements and has the expertise to provide the necessary security measures to keep them compliant. Failure to do so could result in hefty fines, loss of customer trust, and damage to the company's reputation.
Leapfrog not only specializes in helping businesses achieve and maintain compliance, we ourselves also hold several compliance certifications, so that you can trust your information is secure when you partner with us.

How Can We Help?
Protecting your information and your customers’ data is Leapfrog Technology Group's specialty.
- Evaluate - We will perform a thorough evaluation of your business environment, including the technology you rely upon for daily operations. We will look for vulnerabilities and insecure systems within your network, including improper configurations, exposed data, and any malfunctions within your existing security tools.
- Assess - Once the evaluation is complete, we will provide you with your unique, individual Findings Report, showing all of the information gathered in our analysis.
- Implement - Once we have discussed the findings and proposed a strategy for remediation, Leapfrog will implement a complete security plan to provide your business with comprehensive protection for the latest threats.
Schedule Your Initial Cybersecurity Network Assessment Today To Get Started!

Hackers and cyber criminals feed off the misconception that many small business owners hold that the information they are storing is not valuable or potentially dangerous if leaked. Maybe you aren’t storing credit cards and social security numbers, but if you’re storing ANY passwords or personally identifiable information for yourself, your employees or your clients and you’re NOT securing that data, you’re putting a lot of people at risk.
Cyber Insurance is an important precautionary measure you can take for your business, but many businesses find out too late that there are some things that insurance cannot cover. If your company is hit by a malicious ransomware attack, how will that affect your reputation with clients? Will they continue to trust you with their information, or is it possible that public humiliation from cyber criminals might drive a wedge in the confidence they have in you? Many times, cyber insurance has no clause for reputational impact.
Just because you HAVE insurance doesn’t mean you WANT to use it. Hopefully, you have health insurance in place to cover any medical emergencies, but I doubt you’re signing up for elective open heart surgery any time soon! When it comes to cybersecurity, insurance should be a secondary measure AFTER you have made sure your network is truly SECURE.
The worst thing about hackers is that they’re good at what they do. Backups and cloud solutions are necessary measures for data restoration, but they do very little for overall security. Criminals have learned how to sit undetected in a network for an extended period of time – however long it takes to figure out where your data is being stored. Then, once they’ve launched the ransomware, they’ll often destroy backups or remove permissions completely so your data is completely inaccessible, at least, without paying handsomely for it.
Cloud stored data is often similarly targeted by cyber criminals. Unfortunately, providers are only responsible for infrastructure security, NOT for the security of the device accessing the cloud. If a device is attacked, it has access to the cloud, too.
You see it on the news every day. Major corporations and organizations losing millions of dollars and tons of private, personal information is hung out like underwear on a flagpole. Where the mainstream media has failed, however, is in covering the fact that breaches like these are happening EVERY SINGLE DAY to small and medium sized businesses like yours and mine.
Think you’re too small? What about the small, two-person law firm our security team handled a disaster recovery case for? Feeling that they had no need, or perhaps no budget for security, they left their information wide open for hackers to come in and not only steal all their client data, but to also set the ransom for the EXACT amount of money in their bank account, down to the penny. When the criminals weren’t paid quickly enough, they began taunting their client base, publicly humiliating them while they faced the devastating decision of paying the ransom or closing their doors forever.
If you have valuable information, you need to consider how you are going to protect it.
The only thing worse than having your data stolen and being held for ransom is paying that ransom and STILL not recovering your data. This is an unfortunate reality in 20% of ransomware attacks.
The truth is, ransomware is not all that sophisticated. It’s often hastily thrown together, and there are more cases than you might expect where a cybercriminal might genuinely be willing to release your information but is helpless to reverse the damage that has already been done. At best case scenario, your options even after paying that ransom would be to dish out even MORE funds towards data recovery services.
Worst of all, hackers often leave a back door. We are dealing with criminals here, folks, and if they get the impression that they might have a valuable repeat customer on their hands, they are far more likely to leave a hole for them to reenter when they get done spending all your hard-earned money.
The question is, are you willing to pay the sum just to gamble with your data?

 Contact Us At
Contact Us At


